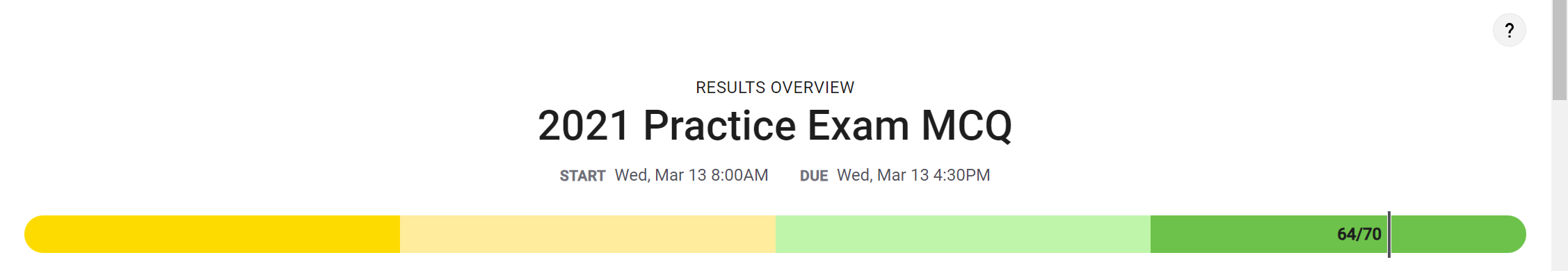
MCQ Score
MCQ Corrections/Reflection
25.In the following procedure, the parameter n is an integer greater than 2. Which of the following best describes the value returned by the procedure?
Correct Answer: The procedure returns the sum of the integers from 1 to n.
Reflection: Upon further inspection this makes sense since j inceases by 1 each time and is added to result meaning that it adds by 1, 2, 3 and so on.
32.Which of the following is a true statement about the use of public key encryption in transmitting messages?
Correct Answer: Public key encryption enables parties to initiate secure communications through an open medium, such as the Internet, in which there might be eavesdroppers.
Reflection: I didn’t know that much about public key encyption but now I know that it establishes secure connection between people communicating online.
50.Which of the following best explains how symmetric encryption algorithms are typically used?
Correct Answer: Symmetric encryption uses a single key that should be kept secret. The same key is used for both encryption and decryption of data.
Reflection: I thought that symmetric meant there would be 2 keys but it makes sense how symmetric means the same key is used for both encryption and decryption.
55.A code segment is intended to transform the list utensils so that the last element of the list is moved to the beginning of the list. Which of the following code segments transforms the list as intended?
Correct Answer: len = LENGTH(utensils) temp = utensils[len] REMOVE(utensils, len) INSERT(utensils, 1, temp)
Reflection: This makes sense since len becomes the length of the list and temp therefore becomes the last element of the list. Then the last element is removed and then inserted at the beginning of the list using temp.
68.The following code segment is intended to remove all duplicate elements in the list myList. The procedure does not work as intended. For which of the following contents of myList will the procedure NOT produce the intended results?
Correct Answer: [10, 10, 20, 20, 10, 10], [30, 50, 40, 10, 20, 40]
Reflection: The code only checks if the element adjacent is a duplicate and when simplified the first list becomes [10. 20, 10] and the second list becomes [30, 50, 40, 10, 20, 40] which still contain duplicates.
70.A programmer wants to create a new string by removing the character in position n of the string oldStr. For example, if oldStr is “best” and n is 3, then the new string should be “bet”. Assume that 1 < n < len(oldStr). Which of the following code segments can be used to create the desired new string and store it in newStr?
Correct Answer: left = substring(oldStr, 1, n - 1) right = substring(oldStr, n + 1, len(oldStr)) newStr = concat(left, right)
newStr = substring(oldStr, 1, n - 1) newStr = concat(newStr, substring(oldStr, n + 1, len(oldStr)))
Reflection: The first code segment works by creatin a left and right segment of the word besides the n letter and then combines it. The second code segment works in a similar manner, but combines the right segment with the combining step.
Popcorn Hacks on Frequently Missed Questions
4.As a popcorn hack (binary challenge), describe an overflow in 8 binary digits
An overflow in 8 binary digits results when the number transmitted is greater than 255. If you add 1111 1111 to 0000 0001, the result would normally be 1 0000 0000 but in 8 bits it would reset to 0000 0000.
5.As a popcorn hack (coding challenge), create a new gate
XNAND Gate Input A | Input B | Output ——–|———|——- 0 | 0 | 1 0 | 1 | 0 1 | 0 | 0 1 | 1 | 1
11.As a hack (binary challenge), make the rgb standard colors
Red: 255, 0, 0 Orange: 255, 165, 0 Yellow: 255, 255, 0 Green: 0, 255, 0 Blue: 0, 0, 255 Indigo: 75, 0, 130 Violet: 238, 130, 238
50.As a popcorn hack (coding challenge), scale list of size by factor of 10 and measure the times n=1000:
Algorithm 2 * N took 0.05 milliseconds Algorithm N^2 took 10.25 milliseconds Algorithm 10 times took 0.07 milliseconds
n=10000:
Algorithm 2 * N took 0.59 milliseconds Algorithm N^2 took 1064.08 milliseconds Algorithm 10 times took 0.10 milliseconds
56.As a popcorn hack (coding challenge) measure the time to calulate fibonacci sequence at small and large numbers Small List:
Version I took 240.00 simulated seconds Version II took 540.00 simulated seconds
Large List:
Version I took 59940.00 simulated seconds Version II took 119940.00 simulated seconds
64.As a popcorn hack (coding challenge), fix the multiply function to work with negative numbers
Code below
'''
As you can see, the function fails when y is negative,
because the while loop condition count < y is never true in these cases.
'''
def multiply(x, y):
count = 0
result = 0
if y > 0:
while count < y:
result += x
count += 1
return result
if y < 0:
while count > y:
result -= x
count -= 1
return result
else:
return
# Test cases
print(multiply(2, 5)) # Expected output: 10
print(multiply(2, -5)) # Expected output: -10, Actual output: 0
print(multiply(-2, 5)) # Expected output: -10
print(multiply(-2, -5)) # Expected output: 10, Actual output: 0
print(multiply(0, 5))
10
-10
-10
10
0
def Ans_A(): # INCORRECT ANS, EXPECTED ANS OF JACKLOPEA
animal = "antelope"[4:8]
animal += "a"
animal = "jackrabbit"[0:4] + animal
print(animal)
def Ans_B(): # CORRECT ANS, EXPECTED ANS OF JACKALOPE
animal = "antelope"[4:8]
animal = "a"+animal
animal = "jackrabbit"[0:4] + animal
print(animal)
def Ans_C(): # CORRECT ANS, EXPECTED ANS OF JACKALOPE
animal = "jackrabbit"[0:4]
animal += "a"
animal += "antelope"[4:8]
print(animal)
Ans_A()
Ans_B()
Ans_C()
jacklopea
jackalope
jackalope